If you want to check an SSH key file to see if it is the same as what is reported as the "Deploy key" by github, this is for you...
From the private URL: https://github.com/<username>/<repo_name>/settings/keys you will see
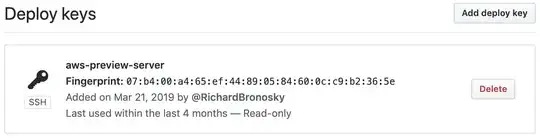
At the terminal:
$ ls -l id*
-rw------- 1 bruno staff 1675 Mar 29 17:03 id_rsa
-rw-r--r-- 1 bruno staff 416 Mar 29 17:03 id_rsa.pub
$ ssh-keygen -E md5 -lf id_rsa
2048 MD5:07:b4:00:a4:65:ef:44:89:05:84:60:0c:c9:b2:36:5e ec2-user@ip-10-2-1-16.ec2.internal (RSA)
$ ssh-keygen -E md5 -lf id_rsa.pub
2048 MD5:07:b4:00:a4:65:ef:44:89:05:84:60:0c:c9:b2:36:5e ec2-user@ip-10-2-1-16.ec2.internal (RSA)
You will notice that you get the same fingerprint for both the private and public keys.
That same command can be combined with a neat feature of GitHub, which is the fact that they publicly serve users' SSH public keys at https://github.com/<username>.keys
Here is a one-liner you can use to take advantage of it.
$ curl -sL https://github.com/RichardBronosky.keys | while read; do echo -e "\nkey #$((++i)):"; ssh-keygen -E md5 -lf - <<<"$REPLY"; echo $REPLY; done
key #1:
2048 MD5:07:b4:00:a4:65:ef:44:89:05:84:60:0c:c9:b2:36:5e no comment (RSA)
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDJGT35gvsFveu+80qgurrLHId0h55E9jliM7Fo0mV9b7eg3EfyagkAcJUSMFkoov3HY4CW0yzOc7WlN57ABwvpRz1ioFDex0n0FkjoSEs5ROeT1OneRK6Bf6XnplgPuQ/LSSkv3kmK6I29R+YWi6TjDvLLoA5BrXJjOMfUv36jxWCDtk/5ZdhMZqhsMuDm06Jg5JBu6n5jQaZkmaIaunz7vOfwVG9LoCI+MYyIdo2S4VTva7Ee7jfAvgSUUgHTjhzsPO0/Ww5a/Kz2ehXW27aJxj/QPLfYR2LmTMbQKm3WpB8P1LjoiU7zjPoVoZ43a4P2JLUDidGKCd3eY5b5xewz
key #2:
2048 MD5:f7:98:f1:0b:73:c6:2a:21:00:7a:70:1d:0f:cf:d8:cc no comment (RSA)
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCQsZrjwKjB4WnE4SwVdDX5eEMxKzPHFBVKKpo9vvWUXRQwdTZy6iVOkyF26IPR+xDPzslzXOClKXUrWEh6La/EMpRwuMrWAbMIJFeDHOb56q4azgopoJmMJHo0yxGu0Ts4XszMACYRhlG6uK2AP5SYiOTp1zKPFjazXAdwLXyOvJurzy6KKuGJdSs/sj9+4uehgyRNOhehCSfg71tJJYwRvO2DDfLgaVEKOgZx58gEnJfhhz9D7rbvdZNhw/hCgtVNJaQF9Mdke2OPwWSo8i0/XNb9Bu/GRXqwMZrxDBhyzieocW40cwuzxWfzoi03aISdtQ1HtawH8+/sswviM1+B
