In this answer I will go through a concrete example. You just need to replace computers' hostnames, usernames and passwords by yours.
Problem statement
Let's assume we have the following network topology:
our local computer <---> server 1 <---> server 2
For the sake of concreteness, let's assume we have the following computers' hostnames, usernames and passwords:
LocalPC <---> hostname: mit.edu <---> hec.edu
username: bob username: john
password: dylan123 password: doe456
Goal: we want to set up a SOCKS proxy that listens on port 9991 of LocalPC so that each time a connection on LocalPC is initiated from port 9991 it goes through mit.edu then hec.edu.
Example of use case: hec.edu has an HTTP server that is only accessible on http://127.0.0.1:8001, for security reasons. We would like to be able to visit http://127.0.0.1:8001 by opening a web browser on LocalPC.
Configuration
In LocalPC, add in ~/.ssh/config:
Host HEC
HostName hec.edu
User john
ProxyCommand ssh bob@mit.edu -W %h:%p
Then in the terminal of LocalPC, run:
ssh -D9991 HEC
It will ask you the password of bob on mit.edu (i.e., dylan123), then it will ask you the password of john on hec.edu (i.e., doe456).
At that point, the SOCKS proxy is now running on port 9991 of LocalPC.
For example, if you want to visit a webpage on LocalPC using the SOCKS proxy, you can do in Firefox:
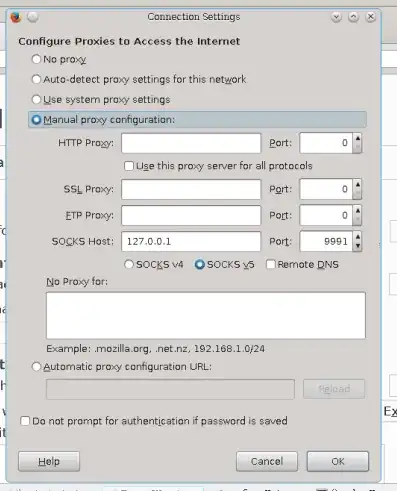
Some remarks:
- in
~/.ssh/config, HEC is the connection name: you may change it to anything you want.
- The
-D9991 tells ssh to set up a SOCKS4 proxy on port 9991.
