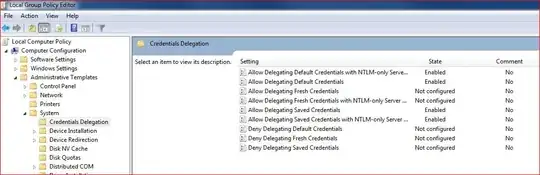
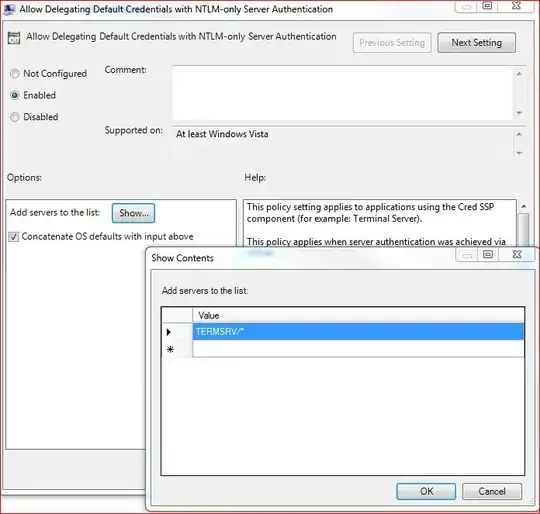
At our office, all of our Windows 7 Clients get this error message when we try and RDP to a remote Windows 2008 Server outside of the office:
Your system administrator does not allow the user of saved credentials to log on to the remote computer XXX because its identity is not fully verified. Please enter new credentials
A quick google search leads to some posts they all suggest I edit group policy, etc.
I'm under the impression, that the common fix for this, is to follow those instructions on every Windows 7 machine.
Is there any way that I can do something via the Active Directory which could update all Windows 7 clients in the office LAN?